The New Insider Threat for Ransomware

Ransomware has become such a lucrative money-maker for individual hackers and large state-sponsored hacking groups that attack tactics are continually evolving.
One of the new ways hackers have found to make this form of malware more profitable is to launch Ransomware as a Service. This is similar to a cloud software subscription service, only it is designed to make it easy for anyone to launch a ransomware attack.
Another new disturbing trend by cybercriminals is to offer a large sum of money to employees inside an organization to get them to release ransomware in the company’s system.
In many cases, this tactic gets attackers past any IT security protections that have been put in place because they entice an employee (“insider”) with access to the system to release the ransomware for them.
The New Ransomware Gang Offering Insiders Money for Attacks
The CyberRisk Alliance’s SC Media site reported that a new ransomware criminal gang tried to solicit the customers and employees of a company called Abnormal Security, asking them to launch ransomware.
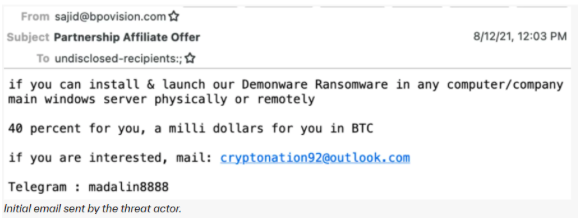
In the case of the employee, the criminals told the person they would pay them $1 million in bitcoin (approximately 40% of the planned $2.5 million ransom demand).
Further, the ransomware group explained how easy it was and that it could be done remotely or physically, trying to entice remote workers.
Here is a copy of the initial email sent that Abnormal Security posted on its website:
Why Employees Conduct Insider Attacks
While no company leaders want to think that their own employees would launch a ransomware attack, insider attacks are all too common. It’s estimated that 60% of data breaches are caused by insider threats.
There are two main reasons that one of your employees may turn on you and take the bait of a large payout for releasing ransomware in the company network:
- They’re disgruntled and have an ax to grind with someone at the company or the company itself
- They don’t have anything against the company but are desperate for money
Employees also might think they won’t get caught, especially if it’s a small or mid-sized company without strong cybersecurity protections in place.
What Are Warning Signs of a Potential Insider Threat?
While not all these are signs that someone is planning to release ransomware in your network, they are potential behavioral red flags to investigate further:
- Accessing company systems during odd hours
- Working strange hours without specific authorization
- Enthusiasm for working weekends, overtime, or unusual work schedules
- Making unnecessary copies of documents
- Showing high interest in areas outside their scope (especially if it’s to do with the company’s IT security systems)
- Vulnerability signs (financial hardship, excessive personal or family medical bills, hostile behavior, history with gambling, etc.)
Tips for Stopping Insider Attacks
Restrict User Permissions
It’s important to use the Rule of Least Privilege when it comes to how you grant user permissions in your system. This rule means giving users the lowest possible access to systems and settings as needed for their job duties.
If you restrict activities, like the ability to install a program on any computer, to only a few high-level admins, then you can reduce your insider risk.
Know the Behavioral Indicators that May Pose a Threat
You can sometimes pick up on potentially vulnerable employees and intervene before they’re faced with a decision about a lucrative offer by a ransomware attacker.
This would include any employees that seem unhappy or complain often as well as employees that are having any kind of financial problems.
Include Insider Threat Awareness in Employee Training
If you make employees aware that your company knows the danger of insider threats and actively monitors for this, they will be much less likely to think they can “get away with it.”
Include insider threat awareness in your employee security training. This lets any potentially vulnerable employees know that your company is watching for this malicious activity. It also helps create a culture where other employees are also watching for potential threats.
Monitor User Activity on Networks
A vital part of good cybersecurity is to monitor user activities on your network. You should have a system that allows you to see who is logging into which company apps and data and when.
This includes when on any device, not just their workstation at the office. You should be managing all mobile devices and monitoring business asset access with a mobile device management application.
Put Ransomware Protection in Place
Make sure you have strong ransomware protection in place, such as a next-gen firewall, email filtering, DNS filtering, advanced antivirus, backup and recovery, and more.
This ensures that you will not be forced to pay a ransom should an attack happen.
Get Help Improving Your Internal User Security
C Solutions can help your Orlando area business put strong access controls and endpoint monitoring in place to ensure you’re properly protected from potential insider threats.
Schedule a free consultation today! Call 407-536-8381 or reach us online.
