How You Can Use the NIST Cybersecurity Framework to Guide Your Business Security

IT security is complex and can involve everything from filtering phishing emails out of employee inboxes to backing up your data so it can be restored in the event of a ransomware attack.
Because there are so many layers to good IT security best practices, it can be easy to miss something important, especially for a small business, who may not have a lot of time.
Just one data breach can be devastating to a small business. Each cyber attack can cost a small company $200,000, plus ongoing costs like loss of customer trust and reputation.
So, it’s important to make cybersecurity a priority and find tools you can use to help ensure you have all your bases covered.
One of these is the NIST Cybersecurity Framework. This is a set of best practices and security guidelines designed to help businesses in any industry sector mitigate their risk of a cyberattack or losses should an incident occur.
Because the Framework comes from a government entity, the National Institute of Standards and Technology (NIST), it’s free for anyone to use to inform their cybersecurity policy and give them a roadmap to follow.
By 2020, it’s projected that 50% of U.S. organizations will be using the NIST Cybersecurity Framework to inform their security practices.
Get Started Using the Cybersecurity Framework
The framework has three main areas that you can use when planning or reviewing your Central Florida company’s IT risk and security strategy.
- Core: These are the activities you’ll perform
- Tiers: This is the level of how you perform them (least stringent to most stringent)
- Profile: This is how well your business is positioned to meet the objectives
We’ll go through how you take advantage of this free resource and use it to help shape and fortify your cybersecurity plan and risk assessment.
Where to Find the Framework
You can download an Excel spreadsheet that provides the Core activities in the Cybersecurity Framework. These are basically the things you need to do to proactively and reactively respond to cybersecurity threats.
You can download the Excel spreadsheet from the NIST site.
Inside, you’ll find a total of:
- 5 Core functions (Identify, Protect, Detect, Respond, Recover)
- 23 categories throughout all the functions
- 108 subcategories
These are designed to guide you to specific activities of cybersecurity best practices you can undertake that cover topics across the broad spectrum of security, including personnel, physical, and cyber.
It’s important to understand that these activities are outcome focused. This means the Framework doesn’t mandate how you achieve the desired outcome, which makes it easy to customize to each organization’s needs.
Understanding the Core Activities
When you open the Excel spreadsheet of the Cybersecurity Framework, you’ll find four key columns.
- The first will include the five functions
- The next will include categories within that function
- Next, will be the subcategories within each category
- Finally, you’ll have standard references to look up for further guidance
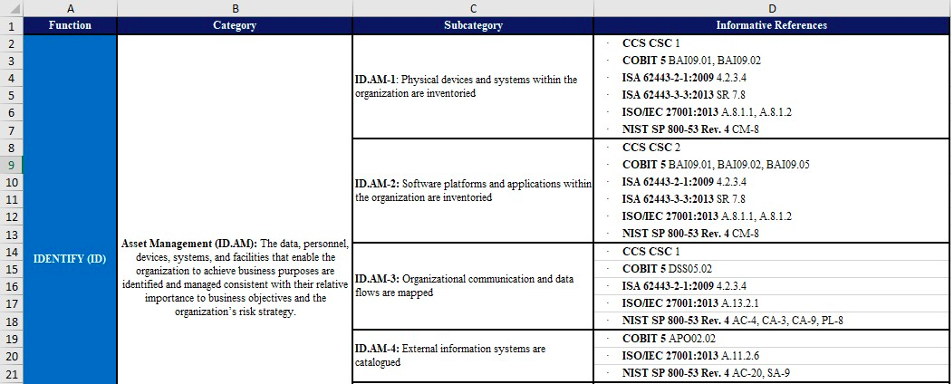
We’ll take a look at the first one that is within the IDENTIFY function.
The category is Asset Management, which speaks to different activities you can perform on assets (data, personnel, devices, systems, facilities) to help mitigate your cybersecurity risk.
The first subcategory in the Asset Management category is a statement that says, “Physical devices and systems within the organization are inventoried.”
What this activity does is ensure that you know all the devices that your company owns and that could potentially be compromised if they were stolen, lost, or breached.
As you go down each of the 23 categories and 108 subcategories to address activities, you’ll be providing several layers to your cybersecurity strategy. Using this Framework helps you ensure you haven’t missed any important safeguards that would leave you vulnerable to a breach.
Using the Informative References
The NIST Cybersecurity Framework is designed to be easy to follow and uncomplicated, which is why it includes informative references in the fourth column of the spreadsheet.
Use these to get more guidance on what to do. We’ll take a look at the first one for the Asset Management subcategory we’ve reviewed above, which is a reference to CCS CSC 1.

This is a reference to the CIS Critical Security Controls, which are a recommended set of actions that give you specific ways to defend against cyberattacks.
CSC 1, which is referenced in the recommendation to inventory all your assets, gives more insight into what to do for this specific cybersecurity activity.
It states, “Actively manage (inventory, track, and correct) all hardware devices on the network so that only authorized devices are given access, and unauthorized and unmanaged devices are found and prevented from gaining access.”
You can see how following the main framework and then accessing the informative references can give you a full roadmap to strengthening your cybersecurity strategy.
Pro Tip: The downloadable Cybersecurity Framework Excel document is editable, so you can copy/paste the details you find at the informative references right into another column in the spreadsheet.
Do You Need Help Strengthening Your Company’s Cybersecurity?
You don’t have to go it alone when it comes to using the NIST Framework to strengthen your cybersecurity. C Solutions can help you review best practices, what you already have in place, and close up any gaps.
Schedule a free cybersecurity consultation today! Call 407-536-8381 or reach us online.
